Okta
Configure Okta single sign-on for your organization
This feature is available to users on our Ultra and Enterprise plans.
Introduction
Follow these instructions to allow your users to login to your Buildstash workspace using Okta.
Create SSO app integration in Okta
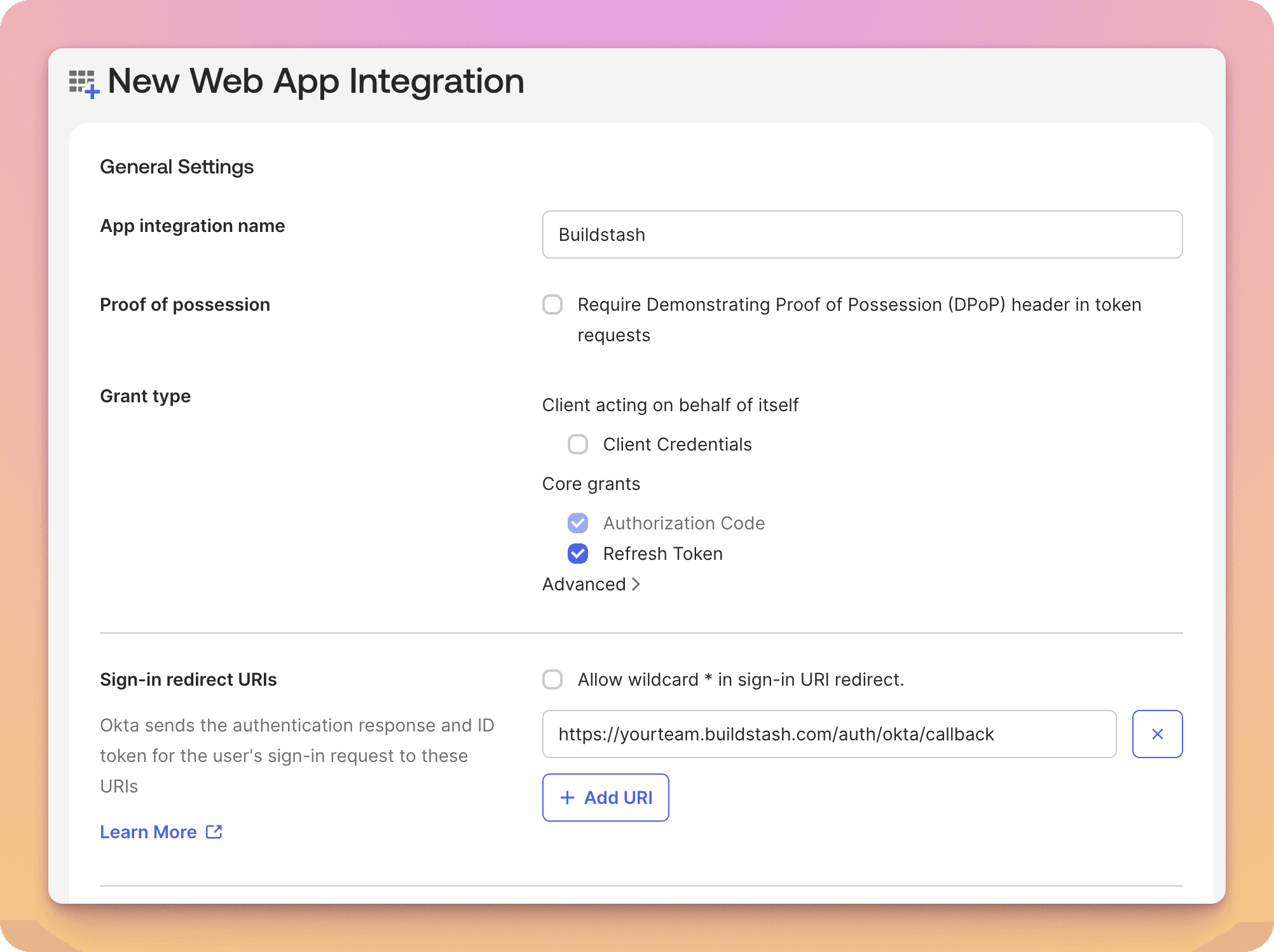
In your Okta Admin Console for your organization, navigate to Applications, and select "Create app integration". In the dialog select "OIDC - OpenID Connect", and "Web Application".

There are some key details to enter when setting up the integration.
The "Sign-in redirect URL" must be entered exactly match the "redirect URI" for your workspace. You can find this in the "Enable identity provider" dialog in Buildstash, covered below. The format will be:
https://{SUBDOMAIN}.buildstash.com/auth/okta/callback
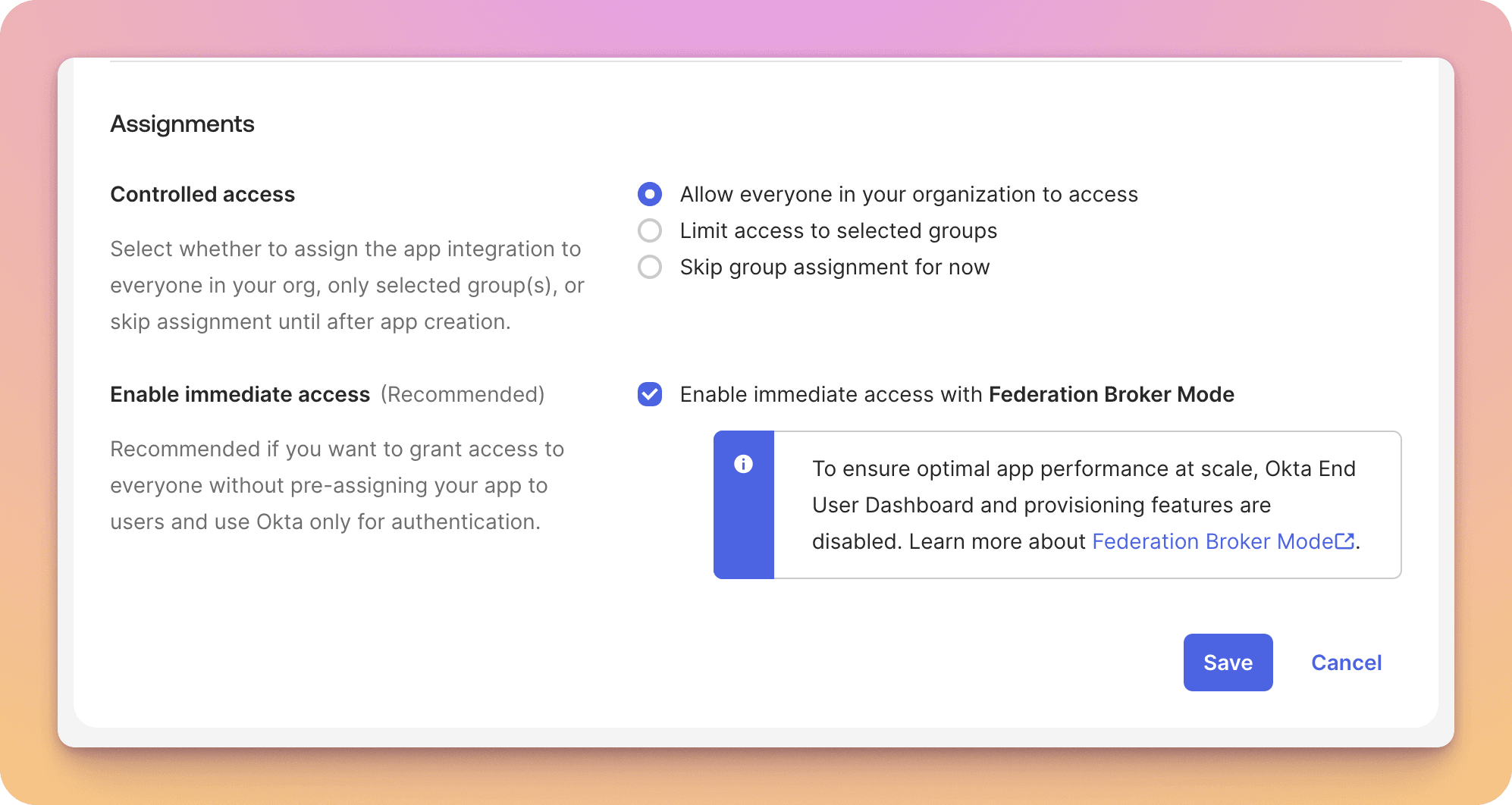
You must also setup access as preferred under Assignments.
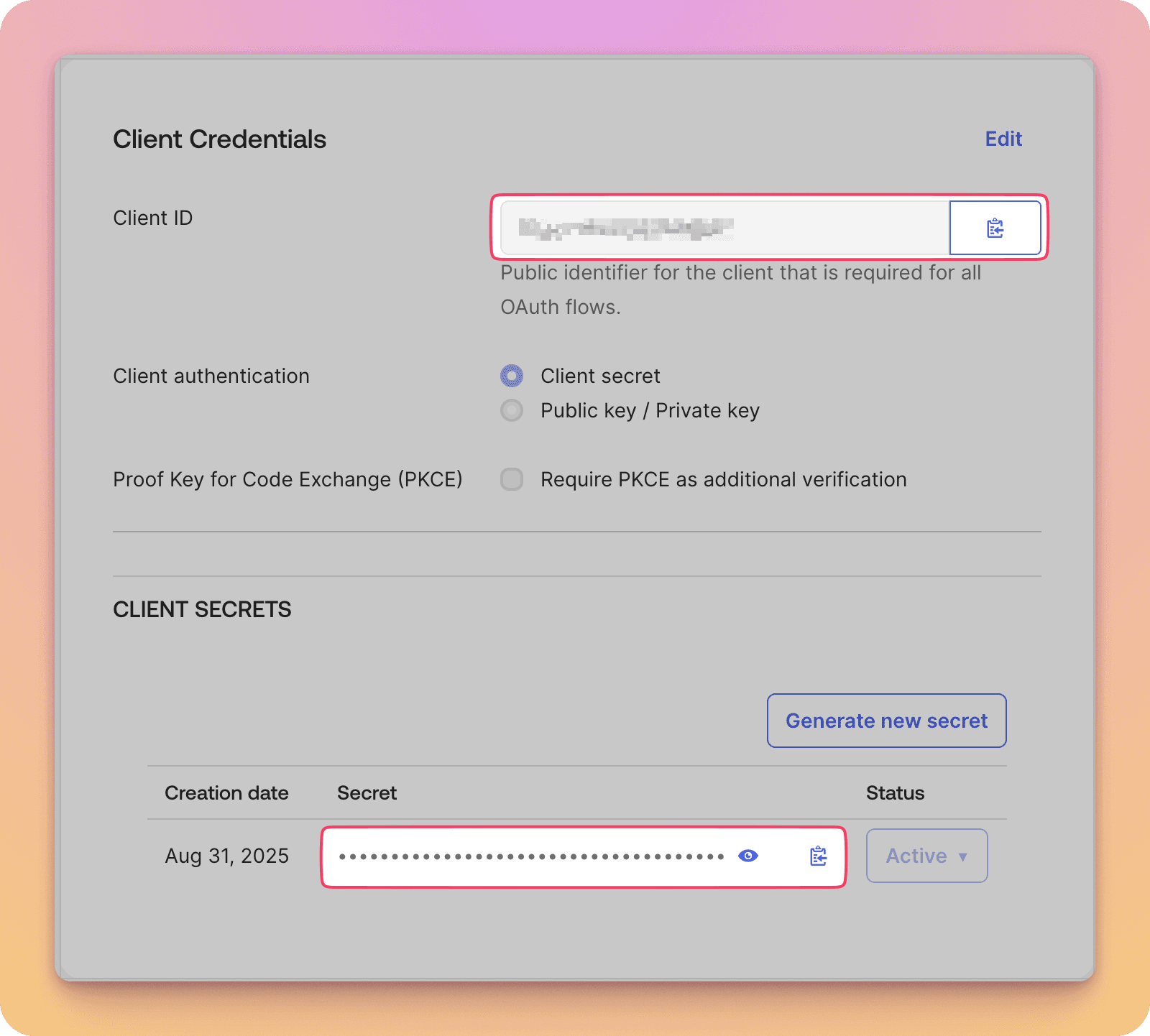
Once the application is created, you'll find the Client ID and Client Secret you'll need to input when setting up in Buildstash later.
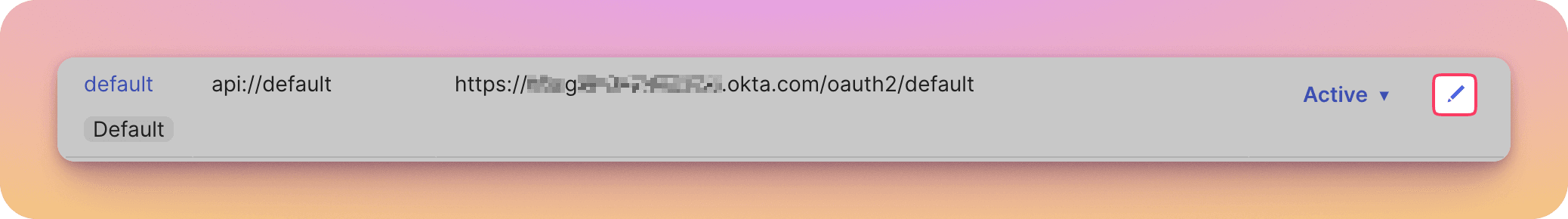
If you've not already setup an access policy on the Authorization Server you wish to use you'll need to do this. Navigate to Security > API > Authorization Servers, then select to edit the Authorization Server you wish to use - this will be the "default" auth server if you've not setup more.
When editing the Authorization Server, go to the "Access Policies" tab, and create a new policy (if you don't already have one), then create a rule.
This is an example of a rule which will provide the necessary access for Buildstash to authenticate.
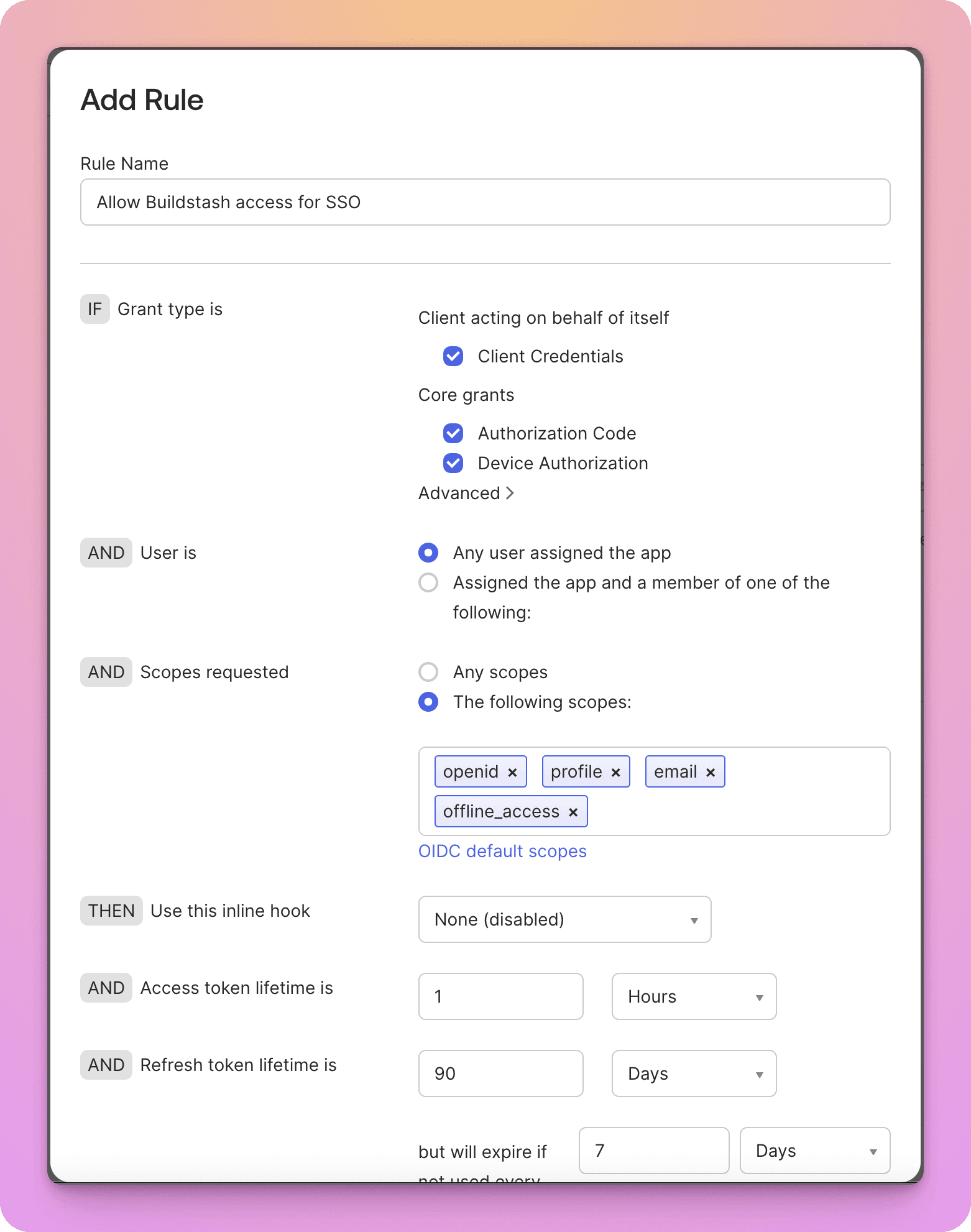
Configure SSO in Buildstash
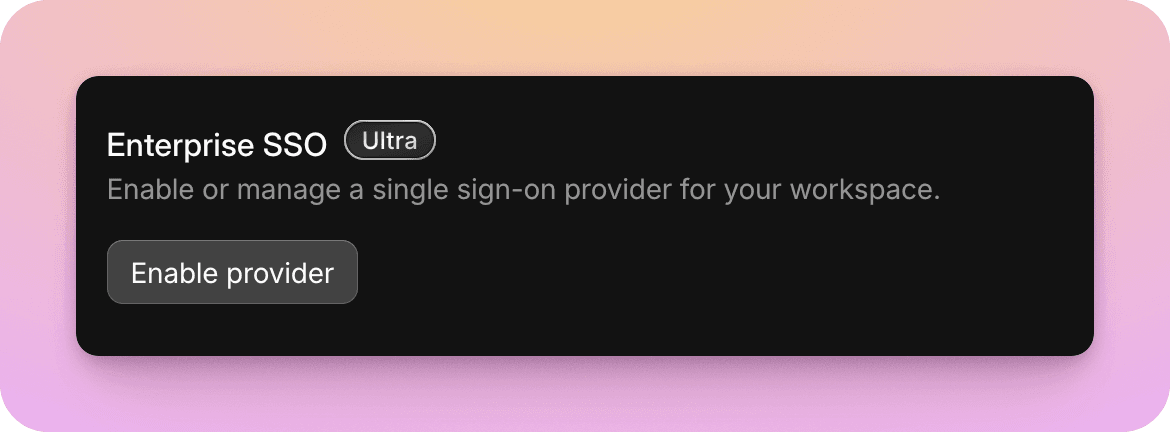
Go to your workspace settings, and under "Enterprise SSO", select "Enable provider".
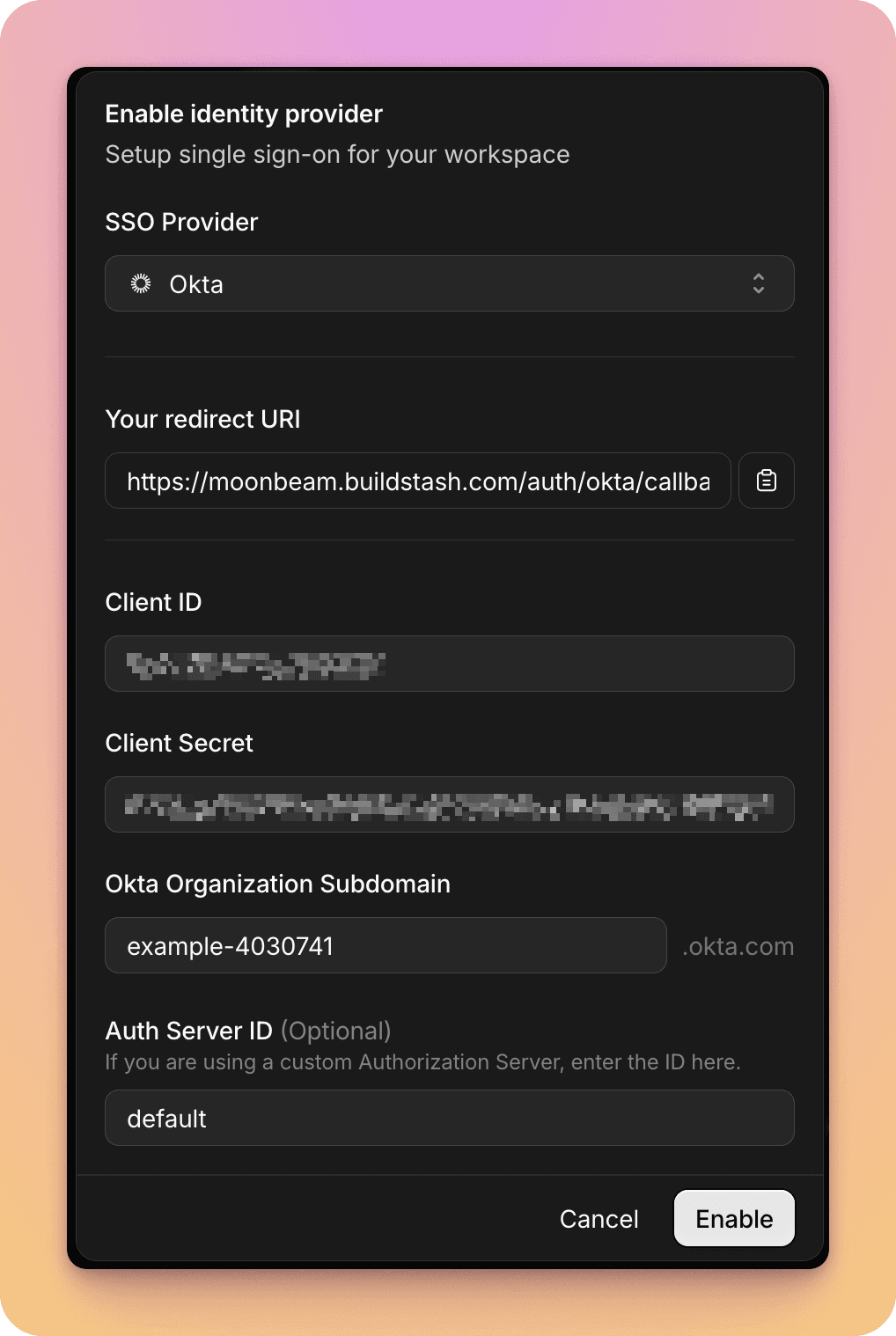
Input the client ID and secret you copied noted from the previous step. Your redirect URI to enter in Okta is also shown here.
You'll also need to provide the subdomain for your organization in Okta, and the name of your Authorization Server. You can find both the values needed in step 4 in the previous section.
Once details are entered and confirmed you'll see Okta connected.
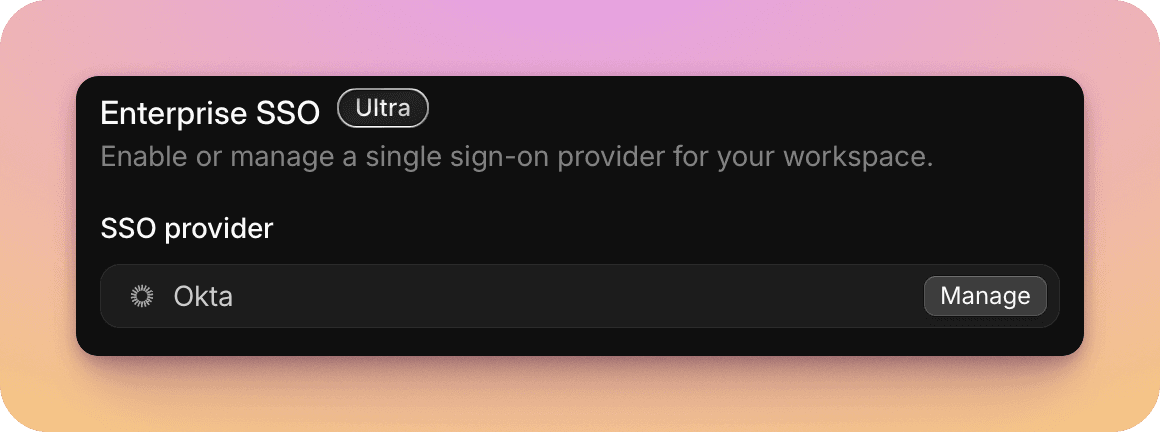
Select "Manage" to update credentials in future, disable non-SSO login, or remove Okta as a login provider in future.
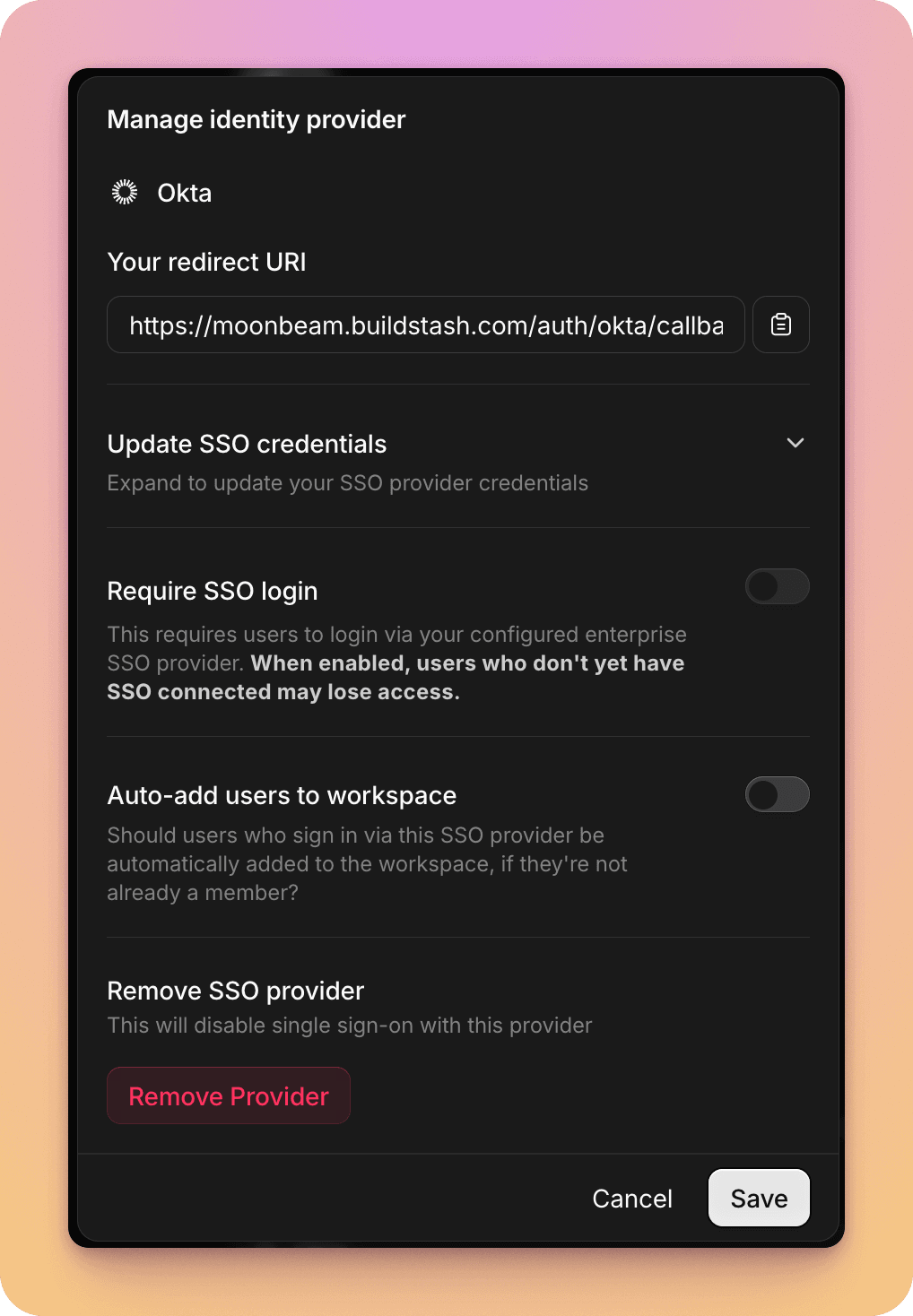
You can optionally require users login via this SSO provider to access your workspace, and there's an option to auto-add users who login via this provider to your workspace if they're not already a member.
You can now navigate to the login page on your workspace custom subdomain, and the Okta SSO option will be presented.